Exploring eBPF – Part 3: Getting Started with Hubble
Learn how to vizualize your network traffic with Hubble and troubleshoot when things go wrong
Learn how to vizualize your network traffic with Hubble and troubleshoot when things go wrong
Use Cilium to ‘mesh’ different Kubernetes clusters together and allow cross cluster Pod to Pod communication in multi-region application architecture.
Learn how to install Cilium on EKS with the getting started guide
Learn how add MetalLB to a cluster with Cilium
Learn how to set up a kind cluster with Cilium
Learn a complete Cilium host policy example for a RKE2-based Kubernetes cluster
Learn how to install Cilium in Kubernetes with KubeKey and visualize network traffic with Hubble
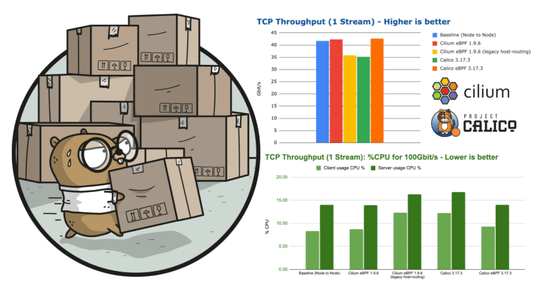
As more crucial workloads are being migrated to Kubernetes, network performance benchmarks are becoming an important selection criteria when deciding what network layer to leverage in a Kubernetes cluster. In this blog post, we'll explore the performance characteristics of Cilium based on extensive benchmarks that we have run in the past few weeks. Upon popular request, we are also including measurements for Calico to allow for a direct comparison.
You've probably heard about the new Man in the Middle (MITM) vulnerability in Kubernetes. If you're unfamiliar, a MITM vulnerability works by redirecting a victim's legitimate network traffic through a secret attacker on the network, where the attacker can eavesdrop or actively tamper with the victim's data before sending it to its intended destination. There have been several MITM vulnerabilities in Kubernetes, most of which take advantage of the default overly-permissive CAP_NET_RAW permissions in Kubernetes. However this vulnerability is unique in two ways:1. MITM attacks generally make use of common types of network vulnerabilities, whereas this vulnerability affects the API layer of Kubernetes itself. 2. Unlike most vulnerabilities that are assigned a Common Vulnerabilities and Exposures (CVE), there's no patch or hotfix you can deploy to protect your environment. This vulnerability is also unique in another way:if you're running Cilium without kube-proxy, you aren't vulnerable to it at all. Let's talk about how.
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace